On December 29, 2016 US-CERT (United States Computer Emergency Readiness Team) had officially released the Joint Analysis Report (JAR) GRIZZLY STEPPE – Russian Malicious Cyber Activity including technical details regarding the tools and infrastructure used by Russian civilian and military intelligence services.
This release prompted me to check our NGO’s website (Maidan Monitoring Information Center) and inspect the logs for traces of such an invasion. My team and I were initially skeptical. However, the results surprised us. We found a system of malicious attacks not described in any reports published thus far.
DETAILS
Our site https://maidan.org.ua is 16+ years old and has lots of unused files. One small.gif is 200 bytes big is a part of an old theme. The file had never been accessed since May 9 2015 until March 11 2016 17:03 (hereafter Kyiv time). Afterwards the small stray file was accessed more than 500.000 times from ~57.000 unique IP addresses. These probes stopped as abruptly as started on December 22 2016 01:04:53.
All probes were similar, the small.gif was the only file requested during one session. Until December all these probes had the same referrer http://i.checkru.net/agent.php (which could had been forged theoretically), since December some probes still had this referrer and some used empty referrer. User agents of these probes were most likely not forged and presented really wide array of infected devices.
I have selectively checked some most actively probing subnets and found that all IPs from yota.ru pool (109.188.*.*) had not accessed any files on server in November other than small.gif. Yota.ru tops the list of providers found in GRIZZLY STEPPE Indicators. I found 497 IPs from this Russian internet service provider involved in the probes of our small.gif, which is more than listed in the IOC. These IPs queried NOTHING on our site, but our small.gif.
I also found visits directly from checkru.net site (188.42.240.30). First visit started on March 10 2016 16:47:09, included several (failed) attempts to find vulnerabilities. During this session small.gif was found. This exploratory session was programmed to find the standard themes for the software used on our site, which is not exotic, but not too common (it is not WordPress, analysis of WordPress hack attempts to follow). Whoever was programming this script researched the software we are using prior to attack.
Scans for vulnerabilities were repeated next day and stopped on Mar 11 2016 17:02:47. Few seconds afterwards the botnet of infected devices started probing our good old small.gif.
Explorer from 188.42.240.30 visited our site on Mar 18 2016, tried new patters of vulnerability scans, failed again and disappeared from our logs until Dec 27 2016:06:58:01, when it tried new pattern and continues to try it one-two times a day until Jan 7 2017.
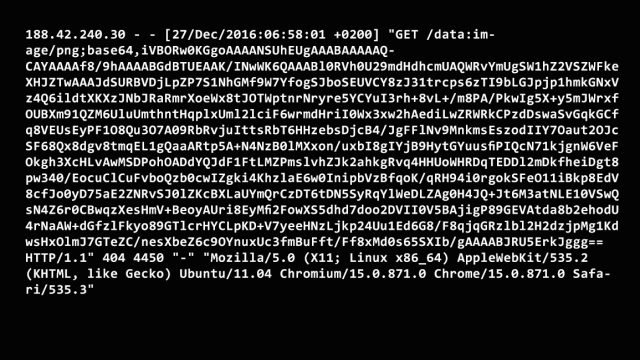
During these sessions explorer used malware samples described in the IOS and similar codes. Explorer did not change the user agent, it may be hardcoded in whatever script they are using. See the sample below:
Probes of small.gif resumed from that IP as well. See the example:
188.42.240.30 – – [06/Jan/2017:13:58:14 +0200] “GET /images/small.gif HTTP/1.1” 200 289 “-” “Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/535.2 (KHTML, like Gecko) Ubuntu/11.04 Chromium/15.0.871.0 Chrome/15.0.871.0 Safari/535.3”
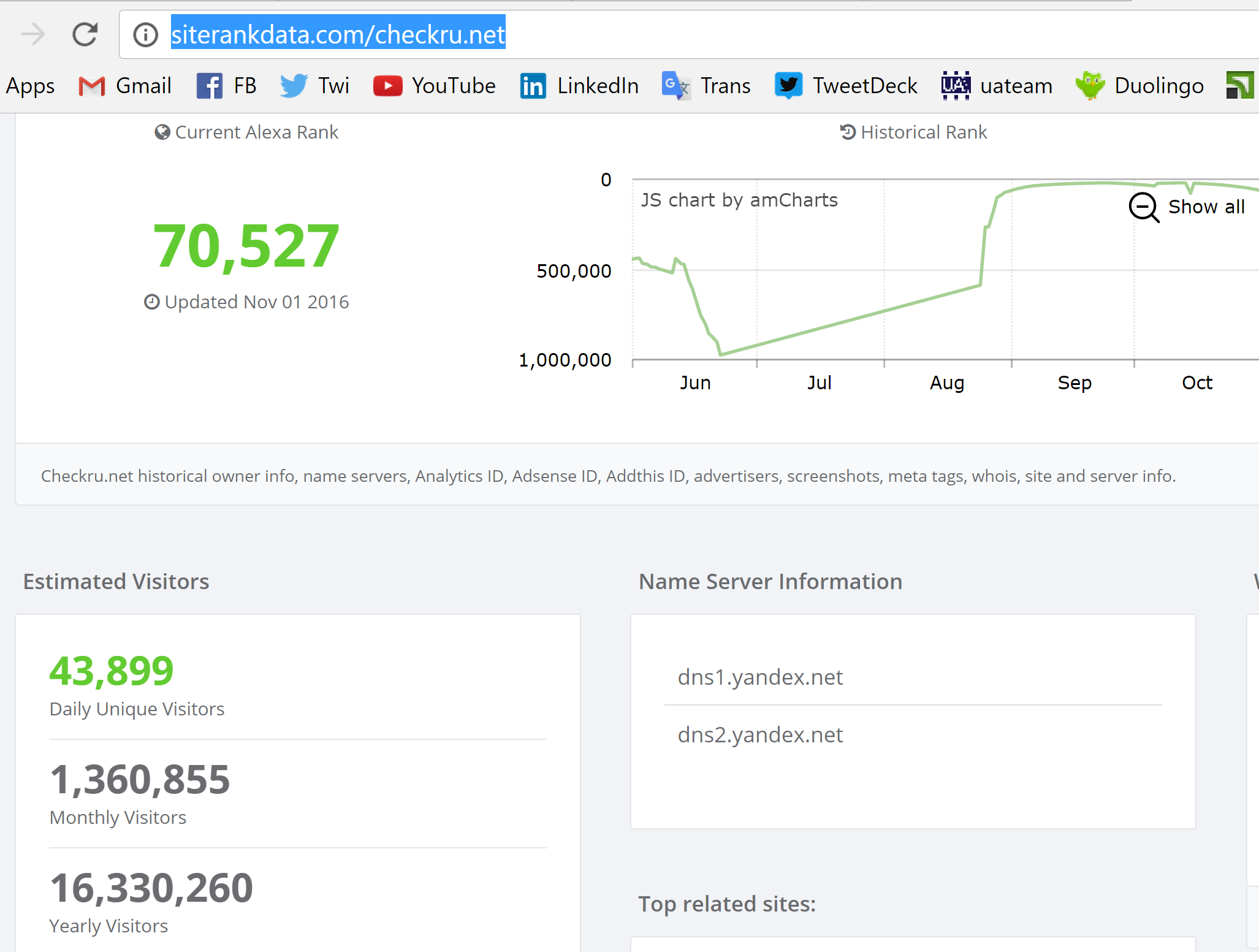
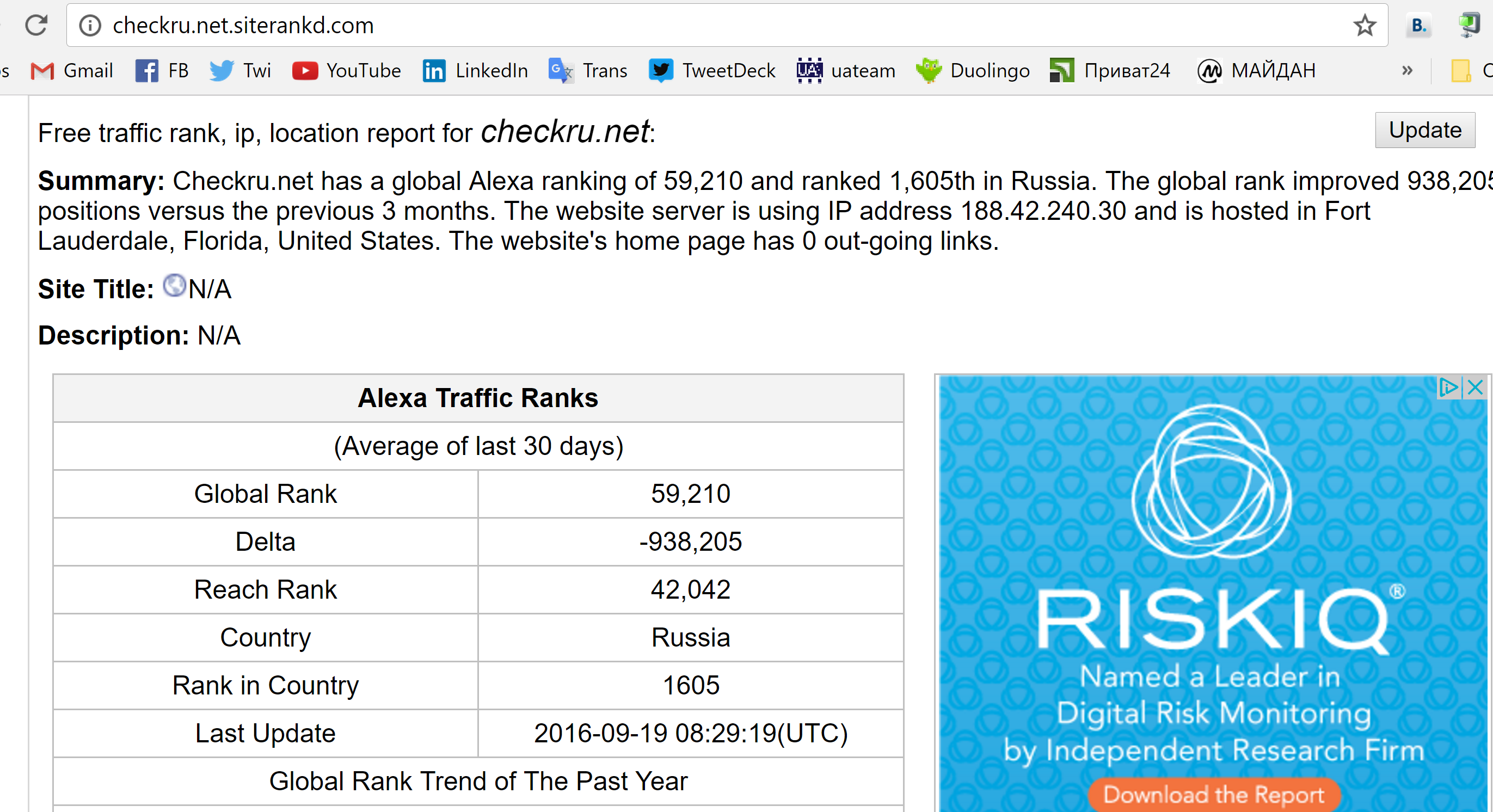
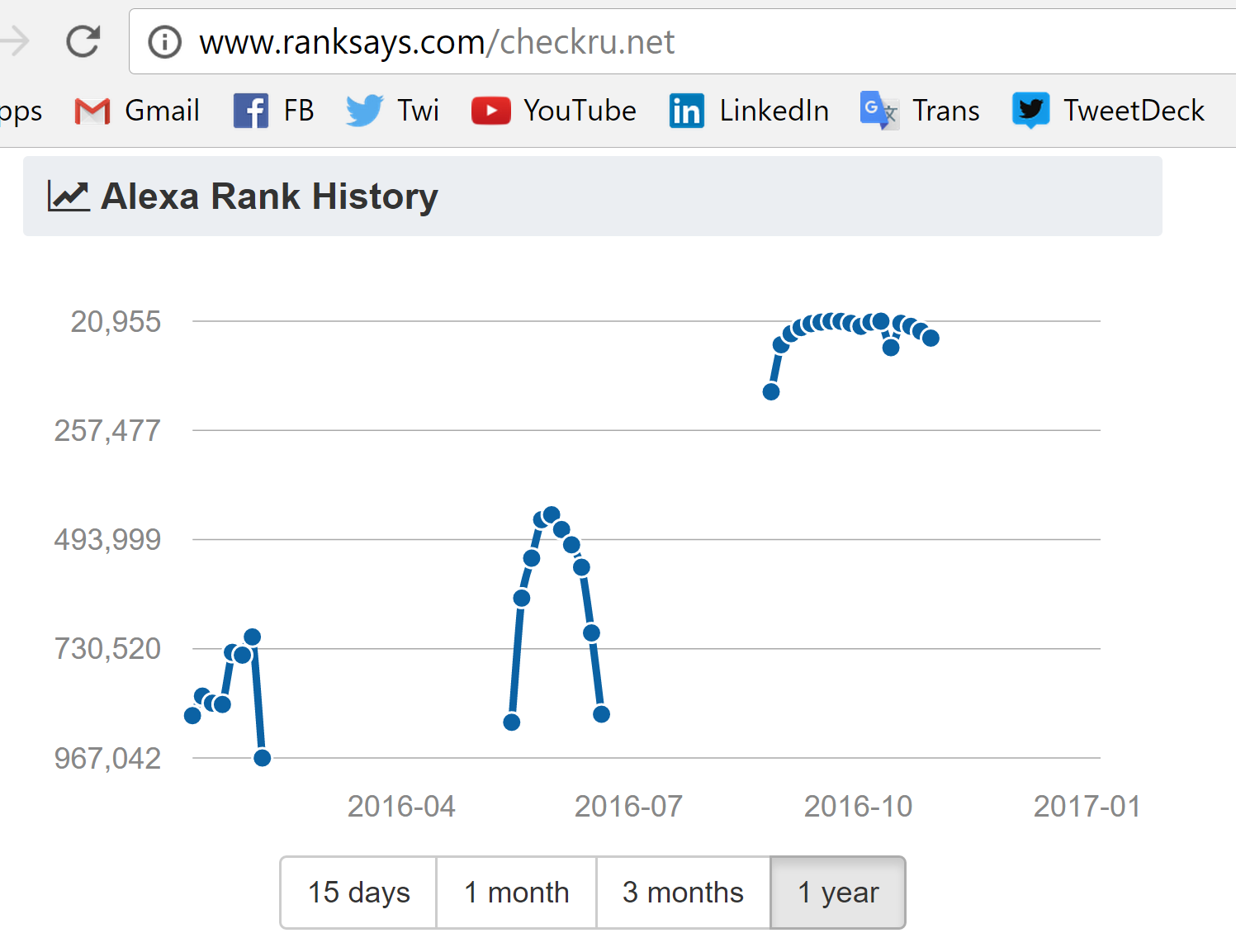
Research for the site http://checkru.net revealed interesting history of traffic associated with this referrer, showing serious peaks with the biggest one in November 2016. That confirms that not only our site were targeted by this mass probes. Most probably there were many such sites. I found public stats of some sites that list considerable traffic from this referrer.
 The site http://checkru.net is in Russian language, it is hosted in the USA, it is served by Yandex DNS. Ownership info is not public. It is more than likely that this site is operated by Russians. I do not know the real purpose of this site, I was unable to make this site to contact our server with any kind of queries from the public interface. I did not register there and did not use their service from inside.
The site http://checkru.net is in Russian language, it is hosted in the USA, it is served by Yandex DNS. Ownership info is not public. It is more than likely that this site is operated by Russians. I do not know the real purpose of this site, I was unable to make this site to contact our server with any kind of queries from the public interface. I did not register there and did not use their service from inside.
188.42.240.30 is not listed in GRIZZLY STEPPE Indicators. I was unable to find any traces of discussion related to this IP or this domain name on the public internet. It may be a botnet coordinator and it is definitely worth researching.
There were three large scale DDoS attacks (more than 50,000 hosts involved) on the Maidan website https://maidan.org.ua December 2007, possibly related to publication that predicted Russian invasion into Georgia, October 2012 – related to documentation of fraud during election to Ukrainian Parliament, January 2014 – related to First Euromaidan’s Forum in Kharkiv. The site is still a subject of regular attacks of various types. We had always attributed these attacks to Russians. Current findings confirm our previous conclusions.
HYPOTHESIS
Other researches have already outlined yota.ru centrality and the fact that one of its owners, businessman Denis Sverdlov, was appointed Deputy Minister of Communications and Mass Communications of Russia.
Therefore, it is reasonable to research the possibility the yota.ru network is used for centralized malicious cyber operations in conjunction with hubs like checkru.net.
NEXT STEPS
Our NGO is eager to share the server logs with appropriate law enforcement agencies in Ukraine and allied countries. I am eager to share more details with security professionals.
Nataliya Zubar, Maidan Monitoring Information Center, Chair
Contact me via pani[AT]maidan.org.ua or http://ua.linkedin.com/in/panimaidan
To be continued…